In our previous articles on Building Information Modelling (BIM) we have explained how information security should be part of implementing BIM for construction projects.
In this latest article we look at how the risks to information on construction and refurbishment projects change over the course of the building lifecycle, and what measures can be put in place to manage those risks.
An overview of BIM
BIM is a process to design a building or structure collaboratively, using a single coherent system of computer models. BIM Level 2 has been mandated for government building projects since 2016 and this calls for “collaborative 3D BIM”. This includes the use of 3D models used by all team members and with project and asset-related information (together with associated documentation and data) being electronic.
This information will be held in a variety of different formats, in hard copy, digitally and used by people in conversations (telephones and meetings). It will be stored, processed and transported in those formats in many different ways; data exchanges as file transfers, e-mails and attachments, and processed in tools (such as modelling tools and databases).
Commonly, information is shared using a Common Data Environment (CDE), which contains tools such as model viewers, document management, tendering, database and messaging functions.
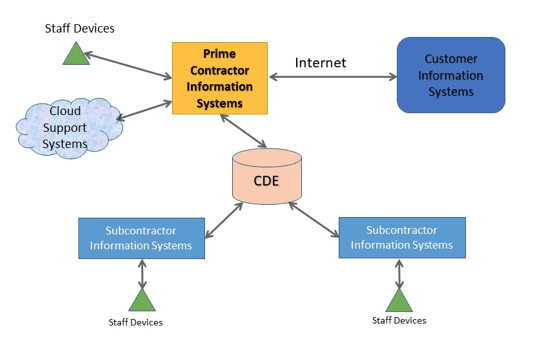
Teams can work collaboratively within the CDE but will also create and store development artefacts (and associated documentation) on their individual company IT systems and on their own devices (laptops, tablets and smartphones). Importantly, this means that information about a building project will be held in many different locations.
Information security risks
Information about a building may be sensitive (to the customer), but is also fundamental to the delivery of the project, since if the information is not available for any reason (through technical failure or user error,) or is corrupted or incomplete, then the project faces delays, cost overruns and potential financial penalties for contractual or legal reasons.
Information security is a very real requirement for any business activity that relies upon accurate and reliable information to be successful. BIM brings together increasing volumes of very useful and detailed information into a collaboration space where it can be shared.
This same business benefit makes it potentially more vulnerable to loss or damage and with greater potential impacts. Information security includes the risk from cyber-attacks (such as hacking and malicious software) as well as the risks from physical theft. Personnel (within the organisation or in supporting companies) are also vulnerable because they make mistakes and are open to bribery or corruption). Finally, there are the risks of running a complex operation anywhere from environmental concerns like fire, flood and earthquake.
Risk assessment across the building lifecycle
Information security uses a risk assessment process that considers:
- What information is of value and where is it held?
- How could it be vulnerable to loss or damage by malicious or non-malicious forces?
- What are the impacts to the business if it is compromised, corrupted or not available?
Since BIM projects have information to the delivery of the project in various locations, including the majority as a significant concentration in the CDE, then it makes sense that the risks to this information should be clearly understood. With that understanding, managers can decide if action should be taken to manage those risks.
For BIM projects, risks change over the building lifecycle and this should be recognised and reflected in risk management measures. The figure below shows the stages of the building lifecycle as defined by the Royal Institute of Building Architects (RIBA).
What happens is that the volume and detail of the information for the project increase as the stages progress.
Stages 0-1 sees the business case and outline being put together – this involves a limited amount of high-level information (including sensitive costing proposals) shared amongst a reasonably constrained group of team members.
Stages 2, 3 and 4, involve a wider number of commercial companies and individuals as the design options are worked up, developed and finalised.
This will create a considerable volume of very detailed technical information for all areas of the project, the most concentrated being the Mechanical and Electrical schedules which will cover the most significant areas of the design. Volumes of data soar as commonly, a 3D model for a project will be in the order of 2TB of information and often greater. This information must be shared and used by a sizeable, but defined group of people in the design team. At this point any significant corruption or loss of this information would be catastrophic to the project timeline and costs.
It is important that information is shared in a controlled manner by design team members who have a common requirement to access most, if not all, the data. The accumulation of information has to be taken in to account (known as aggregation). BIM produces large volumes of detailed information in a single place (the CDE) and this makes it an attractive target to any potential attacker.
As the project moves into stage 4 – construction, this extensive volume of information must be shared with a rapidly increasing number of contractors and subcontractors, as tasks are tendered and let, to bring in the specialists who will deliver the project.
Not all the information is sensitive all of the time, but each time it is shared at this stage it increases the vulnerabilities to that information. This is because it is the “mercy” of the information security measures of additional companies. Generally, the level of information security awareness decreases the further down the supply chain, as companies get smaller and their motivation for additional cost for security measures reduces. At this point managing data sharing is crucial. For example a bricklaying company does not need the full 3D model with meta data as required by M&E contractors.
Whilst risks can be said to plateau, or even reduce for stage 7 – Handover, they rise again significantly during the longest stage of the whole process – In-Use. Given that a building will be operational for longer than 10 years, the BIM information is exposed to a new group of maintenance and building management companies.
Cyber security issues in this phase include the way in which system support is often conducted remotely, and because new technologies in smart building management have been found, in some cases, to have vulnerabilities which can (and have been) exposed by attackers to compromise both them and linked corporate IT systems. One of the main issues during this period is who owns the risk of the BIM information and who decides how is access to it is controlled.
Managing BIM information risk
So, how can the risks to BIM information be managed during the lifecycle stages? The principles for information security are the same for all stages, but require tailoring and a sharper focus on specifics at some points. The basic principles are:
Early stages:
- Build in information security at the outset. Customers should set security requirements and suppliers should provide information security services as an integral part of their service. Contracts should specify information security requirements such as:
- Non-Functional Security Requirements covering information security;
- Employer Information Requirements;
- A Security Aspects Letter – produced by the customer, for the contractor and which lists sensitive information assets and their values.
- Identify and value sensitive information assets:
- Know what information is sensitive, why, and where it is;
- Determine customer protection priorities;
- Identify and assess risks:
- Assess if you have information that should be protected;
- Understand the requirements for information availability and integrity and not just confidentiality (who is authorised to access it);
All stages:
- Include responsibility for information security in the wider governance structure:
- Supplier + customer cooperation.
- Control Information sharing
- Common naming conventions and security gradings.
- Balance need to share balance with need to know;
- Access controls within the CDE;
- Manage all forms of data information sharing.
- Roll down information security to supply chain companies;
Basic information security measures;
- Monitor and manage information dissemination.
In use:
This is the typically long period of time when the building is in use and when the building itself, and the customers within it, can be exposed to attackers who exploit:
- Information compromised during the build stages;
- Building management systems with existing vulnerabilities form the build stages or which become vulnerable because they are not maintained or updated;
Information risk management is not just about technical security measures but includes physical (control of entry, alarms, CCTV), personnel (security checked management teams) and procedural measures (e.g. governance, resilience procedures and effective support processes).
Given the length of time that a building is in use, and the way in which it is used and by whom changes, it is essential that risk assessments and corresponding risk management measures are reviewed and updated to suit.
Summary
BIM is about sharing more information more widely to increase the efficiency and reduce costs of a construction project. Information sharing must be managed to a practicable degree. This doesn’t necessarily mean restricting information sharing, but rather understanding it and balancing the risks.
The customer needs to be more intelligent about putting information security requirements into BIM projects at the outset in contracts.
Suppliers need to be more intelligent about information security and make this part of their service offering, to both support the customer in understanding the risks, and ensuring that their own IT project delivery systems are not exposed unduly to the consequences of information loss, corruption or exposure.
Good information security must cover the entire lifecycle of the built asset, especially the In-Use phase. Information security is constantly evolving, and todays measures may not be adequate in 5 years’ time. Good governance and the management of risk is essential throughout the lifecycle and needs to evolve over time.
Guidance on BIM and information security is available from a variety of sources:
Centre for the Protection of the National Infrastructure: PAS1192-5, and a variety of other good practice information and guidance – http://cpni.gov.uk/
The Institution of Engineering and Technology: Code of Practice for Cyber Security in the Built Environment – http://theiet.org/
How Ascentor can help
Ascentor has experience in developing a strategy for implementing the security aspects of BIM .
We understand the information security concerns around integrating sensitive information in models that have to be shared digitally with multiple users and have developed a pragmatic approach to assessing and managing the risks of BIM in Common Data Environments and down through the supply chain companies.
We can help organisations either as intelligent customers seeking to ensure that their information is secure during such projects or as intelligent suppliers demonstrating that they can manage customer information in a challenging scenario.
For further information
If you have found this article interesting, the Ascentor blog regularly carries articles about BIM and other cyber security issues. You might also like to keep in touch with Ascentor by receiving our quarterly newsletter.
If you’d like to discuss the topic of BIM in more depth or any aspect of IA and cyber security, please contact Dave James, MD at Ascentor.









