The case for a considered approach to Information Assurance on MOD projects
Industry Security Notice 2023/09 advises “Delivery Team Leaders must plan and document the security approach. This document must be maintained during the life of the capability and transferred to the Capability Owner prior to the capability entering service.”
Which means what exactly – leave this to the last minute and produce a side of A4 with a brief description or summary? We would suggest not, as this is a more complex, detailed, and business-critical component of the programme delivery.
“What’s the problem?” you may ask. Well, in this article, we’ll explain.
We’ll make a balanced case for why your approach to Information Assurance (IA – making sure your information stays secure) would benefit from a more holistic approach.
What is a Security Approach Document?
Systems, services or devices designed to handle classified information need to be “assured” so they adequately mitigate the risks of compromise to the confidentiality, integrity and availability of the data.
The most recognised approach is to follow a suitable risk assessment methodology, there are many but among the more popular are NIST 800-171, NIST 800-53 (if you live in a Defence world) and capture the outcomes as part of an ‘evidence pack’ for the Senior Risk Owner (SRO) to use as a basis for a go/no-go decision i.e. provision of an assurance decision, or not. The evidence pack may be referred to as a Security Definition Management Document (SDMD), for example.
The SDMD sets out the system, the identified risks, and applied security controls. An appointed Delivery Team Security Lead compiles the document, which the SRO reviews and, if all is well, gives final sign-off.
So, what’s wrong with that?
Sounds fine and, for a simple system, it may be fine. But here’s a list of things that make an SDMD in isolation a potentially dangerous weapon:
- As with the old-style Risk Management Accreditation Document Set (RMADS) approach, there is still an opportunity for this to be done at the end of the project as a “wrap-up” exercise, undertaken in the dismissive tenor of the opening sentence;
- It can focus on compliance for the sake of compliance “a compulsory tick-box” exercise;
- It can be a stand-alone, one-off exercise often shelved and forgotten once finished;
- It is heavy on process and documentation;
- It is often written in technical, jargon-ridden language;
- It is resource heavy and so perceived as expensive;
- It is likely to be outsourced, meaning there is potential for minimal interaction between the author and the system owner;
- While ISN 2023/09 stipulates the security approach must be documented, there is no set template for this, introducing the risk of non-standard, ‘detail light’ documents being produced.
Which all adds up to something that may cost a lot and be of limited business value. Ironically, it may even result in a system with poor security. To draw a parallel, ISO 9001 certification only means you have a set of processes in place, and you follow them, not that they are efficient and effective processes or that you are a better business for it.
And, to cap it all, by leaving it to the end, you are simply documenting what’s been done rather than proactively identifying and mitigating the information risks.
Don’t get us wrong, we are not saying that an SDMD is a bad thing, but just producing an SDMD as part of the completion process leaves much to be desired. It needs to be part of a balanced and rounded approach.
What else can be done?
Well, the opposite of the list above. In accordance with JSP440 and ISN 2023/09 and in line with Ascentor’s philosophy, IA and assurance should follow the Pragmatic, Appropriate and Cost Effective (PACE) principle which caters for early engagement in the CADMID lifecycle to understand the system requirements and to begin to appreciate potential risks/issue from a projects onset.
To achieve PACE, the Delivery Team Security Lead function, responsible for IA on projects, must be an integral part of the delivery team and must get involved early.
Projects will range from complex to straightforward. Equipment Programme (EP) projects are typically complex, as are some UCR (Urgent Capability Requirement) to Core projects. These complex projects demand a structured approach to IA delivery. Activities and products need to be defined based on where the project is within the Concept, Assessment, Demonstration, Manufacture, In-Service and Disposal (CADMID) cycle.
This ensures IA is appropriately applied at the correct stage, mitigating project risks of failing to achieve Initial and Main Gate approval and system accreditation. It also reduces financial exposure to the consequences of re-engineering technical security solutions.
By following robust IA processes, the IA requirement can be optimised before an Invitation to Tender (ITT) is issued to potential suppliers, thus ensuring IA is considered in the proposal and appropriately costed and built into the design.
At the other end of the scale, UCR projects and projects, where commercial-off-the-shelf (COTS) equipment is being procured without modification, do not require such a structured approach to IA. In these cases, the MOD is buying a product with technical security already included, so there is little if any, opportunity to add it in.
The focus here relies on developing PACE processes and procedures that may modify the end users’ tactics, training and procedures. Hence, a simpler, less expensive approach is more appropriate – perhaps in these cases, just an RMADS is enough.
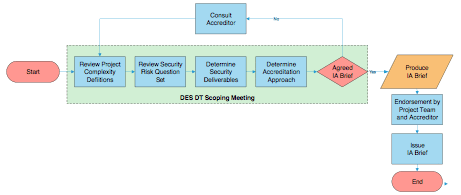
Projects may fall firmly into either the complex or straightforward category, or maybe a hybrid somewhere in between. A flexible approach to achieving PACE that caters for all different types and sizes of project is based on the concept of a triage process, as shown in the diagram below.
Using this process, the Delivery Team Security Lead assesses each project for its IA characteristics with full stakeholder involvement (including the project team, the SRO and the information asset owner). Together they reach a consensus on which approach offers a PACE solution and identify what benefits can be derived. Whatever approach is decided, the risks and how they are mitigated need to be understood, and the residual risks exposed.
An SDMD may well be the chosen medium but that will depend on the complexity of the system, the IA approach taken, and the preference defined by the Accreditor. The decision is reached through an informed and considered process; it is not simply a forgone conclusion.
How Ascentor can help
For 12 years, Ascentor has provided IA and accreditation services to HMG departments including implementing triage processes and supporting MOD EP, UOR, and UOR to Core projects. Many IA consultancies can offer certified staff who understand compliance, but few can rival our drive for IA to bring true benefit and ensure it does not become a burdensome, resource-hungry activity, blindly following process and policy.
Earlier in this article, we referred to the idea of an SAC function. We used the term “function” deliberately as the traditional SAC role can be substituted with an SAC team or service. We have successfully implemented this in MOD delivery teams to bring:
- Skilled and qualified consultants working full time in IA and accreditation, which lowers the risk of appointing short-tenure or temporary MOD SAC cover.
- Flexibility and experience to handle different types and sizes of project.
- Resilience and agility to scale up and down as demand for SAC services changes.
- Value for money by applying the PACE principle in each situation.
For more information, please read Tips for Security Assurance Coordinators on MoD projects.
For further information
If you have found this article of interest, the Ascentor blog regularly carries articles about Information Assurance (IA) and cyber security issues. You might also like to keep in touch with Ascentor by receiving our quarterly newsletter.
Should you wish to gain further advice on your IA and accreditation or just generally improving your cyber security maturity, please contact Dave James, MD at Ascentor.









